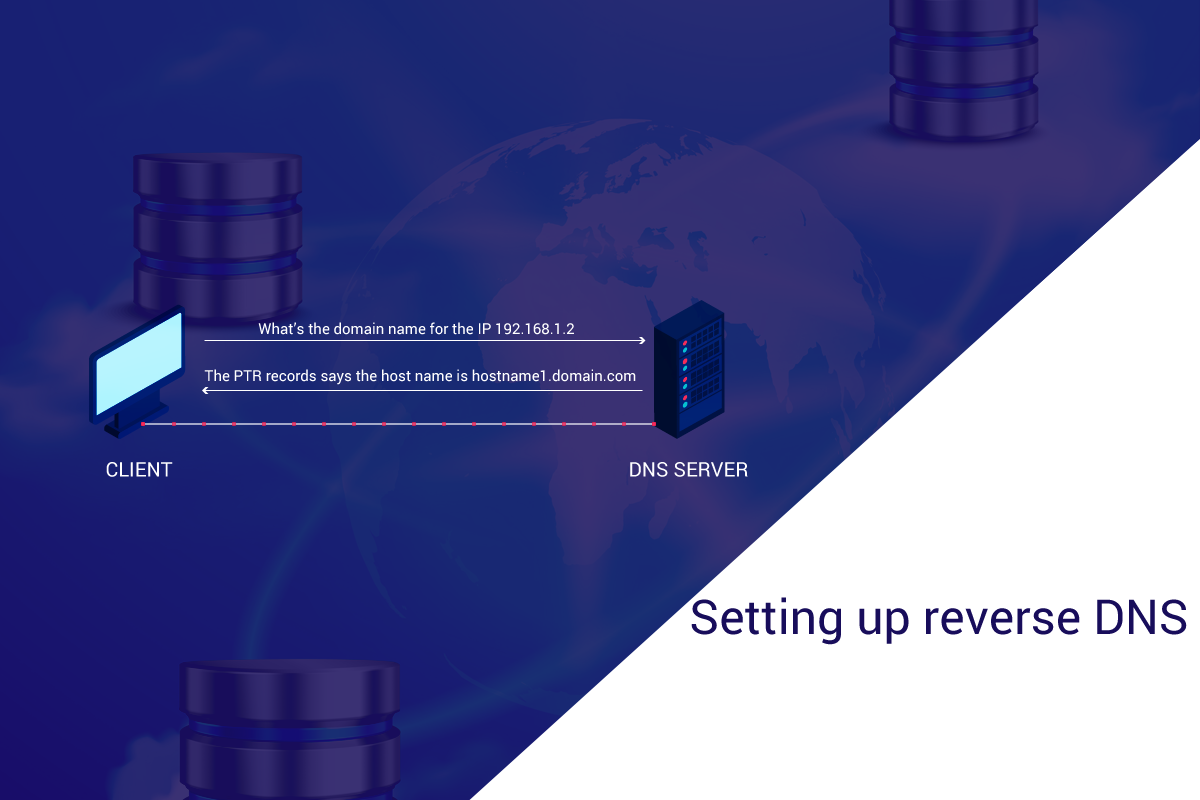
Setting up Reverse DNS Without The Help Of Data Center
In most cases, the rDNS setup will be done by the Data Center (DC) technicians. But in case if the DC delegates it to a support team like us, you have 2 choices – to leave it in the hands of server management expert like us or to do it on your own and in which case, this blog post might come handy. Come let’s see what it takes for you to setup the rDNS by yourself.